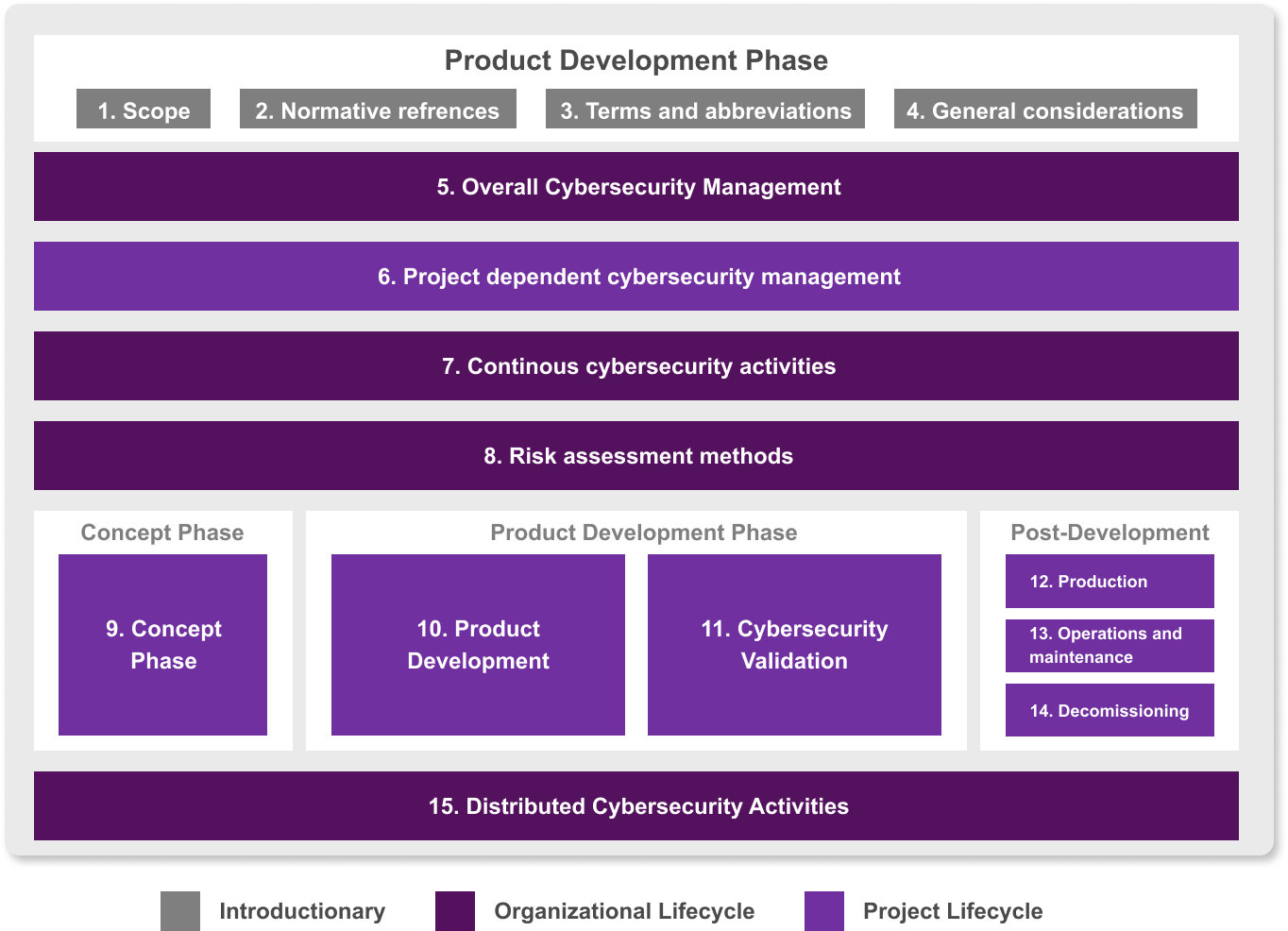
Cybersecurity in Automotive compliance
IBM ELM and Softacus offer solution to the important part of Automotive Compliance – Cybersecurity. Learn more about the advantages of using IBM ELM Automotive Compliance in relation to Cybersecurity in this article.

Cybersecurity Management System
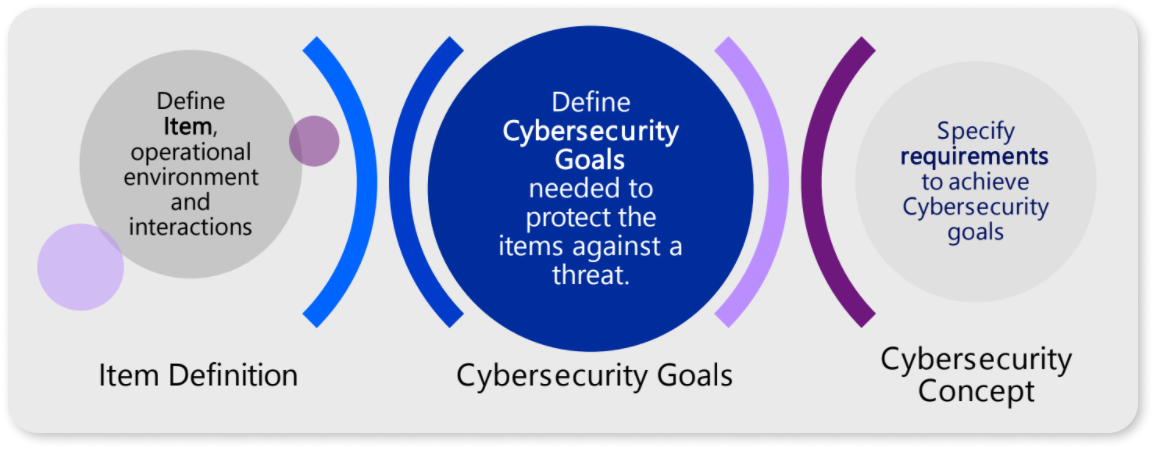
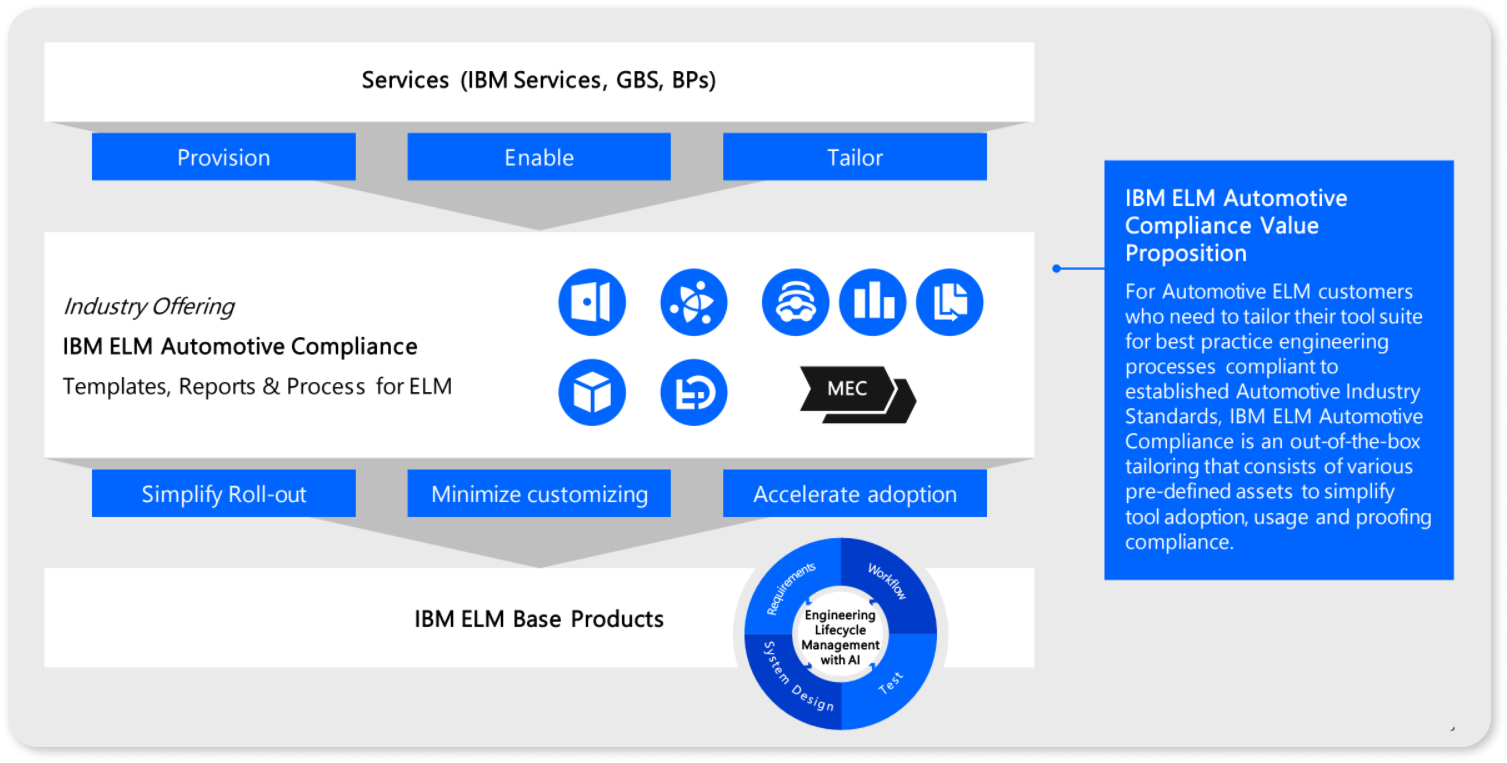
IBM ELM Automotive Compliance provides support to setup Cybersecurity Management System to comply with UNECE WP.29/R.155 regulation by supporting compliance ISO/SAE 21434 with focus on cybersecurity concept including Threat Analysis and Risk Assessment (TARA) and Systems and Software Product Development.
ELM Automotive Compliance
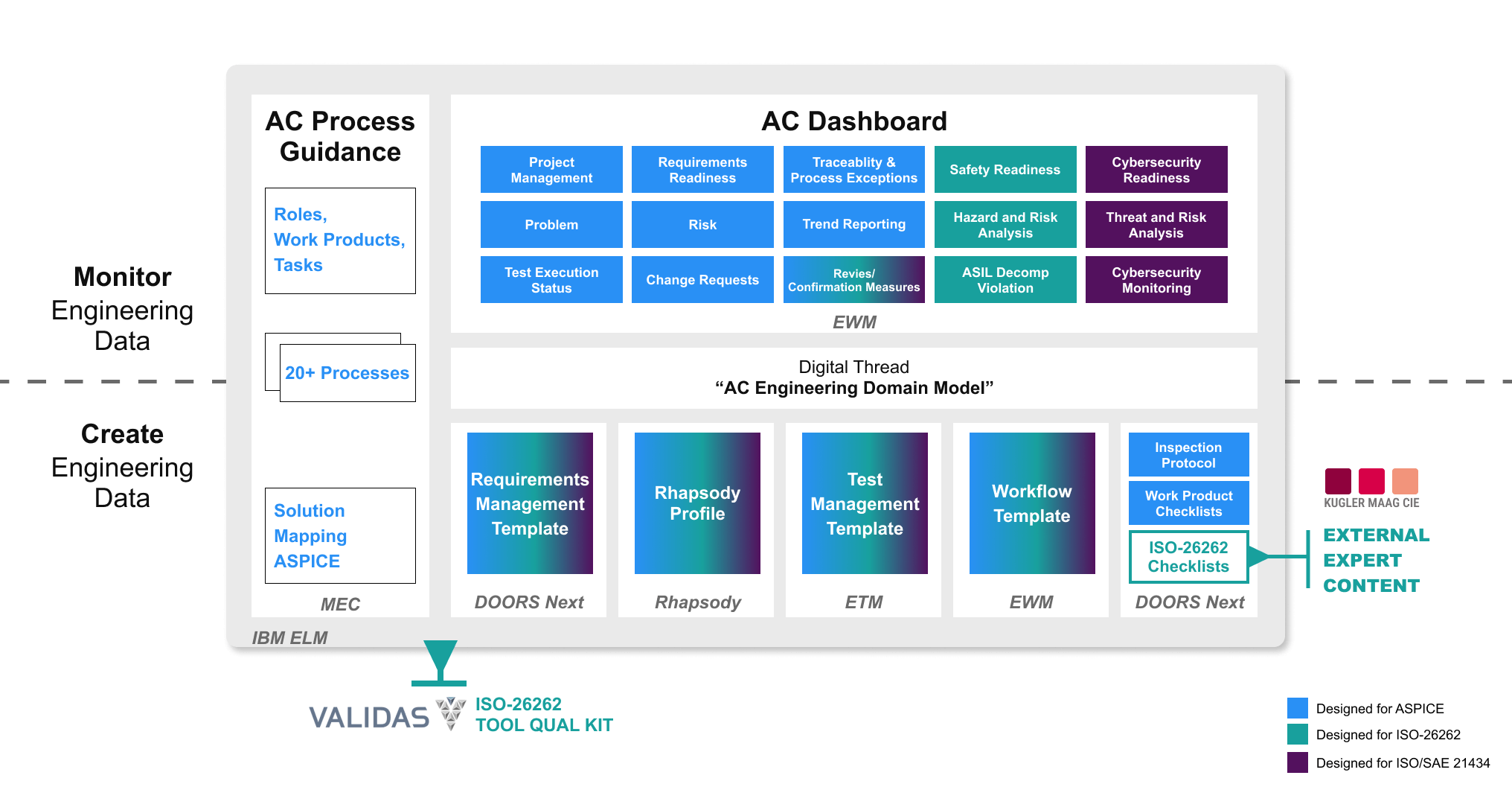
The ELM Automotive Compliance significantly reduces the costs for audit preparation and compliance with automotive standards. The pre-defined, Automotive Systems Engineering process with built-in process guidance is:
- Designed to provide a detailed mapping of work products in ISO/SAE 21434
- Provided with continuing industry transformation in mind and rely on established SAFe Agile process framework.
- Built to fit the out-of-the-box process content to your own needs required to achieve higher level of process maturity
Support for
HARA
Explicit support for Hazard Analysis and Risk Assessment (HARA) via automized ASIL value calculation
Capturing of Safety Elements
AC data model supports capturing of the safety elements required by ISO 26262 (e. g. Item Definition, Hazardous Events, Safety Goals, Safety Requirements)
Pre-defined
HARA format
Teams benefit from improved consistency because of the pre-defined HARA format and automized ASIL Value calculation
Template Compliant to ISO 26262
Engineers save time performing HARA because they can rely on a pre-defined template compliant to ISO 26262
ELM Automotive Compliance -
Ready for Automotive Regulations
Cybersecurity part of the Mission
Drive
Compliance
Compliance should be a by-product, not an additional effort
Consistency, completeness, and correctness can be demonstrated for compliance.
Improve
Clarity
Documented Process should drive implementation
Break down tool and process barriers.
Establish
Governance
Maintain common understanding on progress against project and technical objectives with the stakeholders.
Deliver
Frequently
Reduce time to market by supporting iterative development
Drive Economic value to deliver the right things first.
ISO/SAE 21434
Standard for Cybersecurity
Whats new?
- AC data model was extended to foresee capturing of the cybersecurity risk elements required by ISO/SAE 21434 (e. g. Item Definition, Asset, Threat Scenario, Damage Scenario, Attack Path, Cybersecurity Goals, Cybersecurity Requirements)
- Explicit support for Threat Analysis and Risk Assessment (TARA) via automized calculation of values during TARA
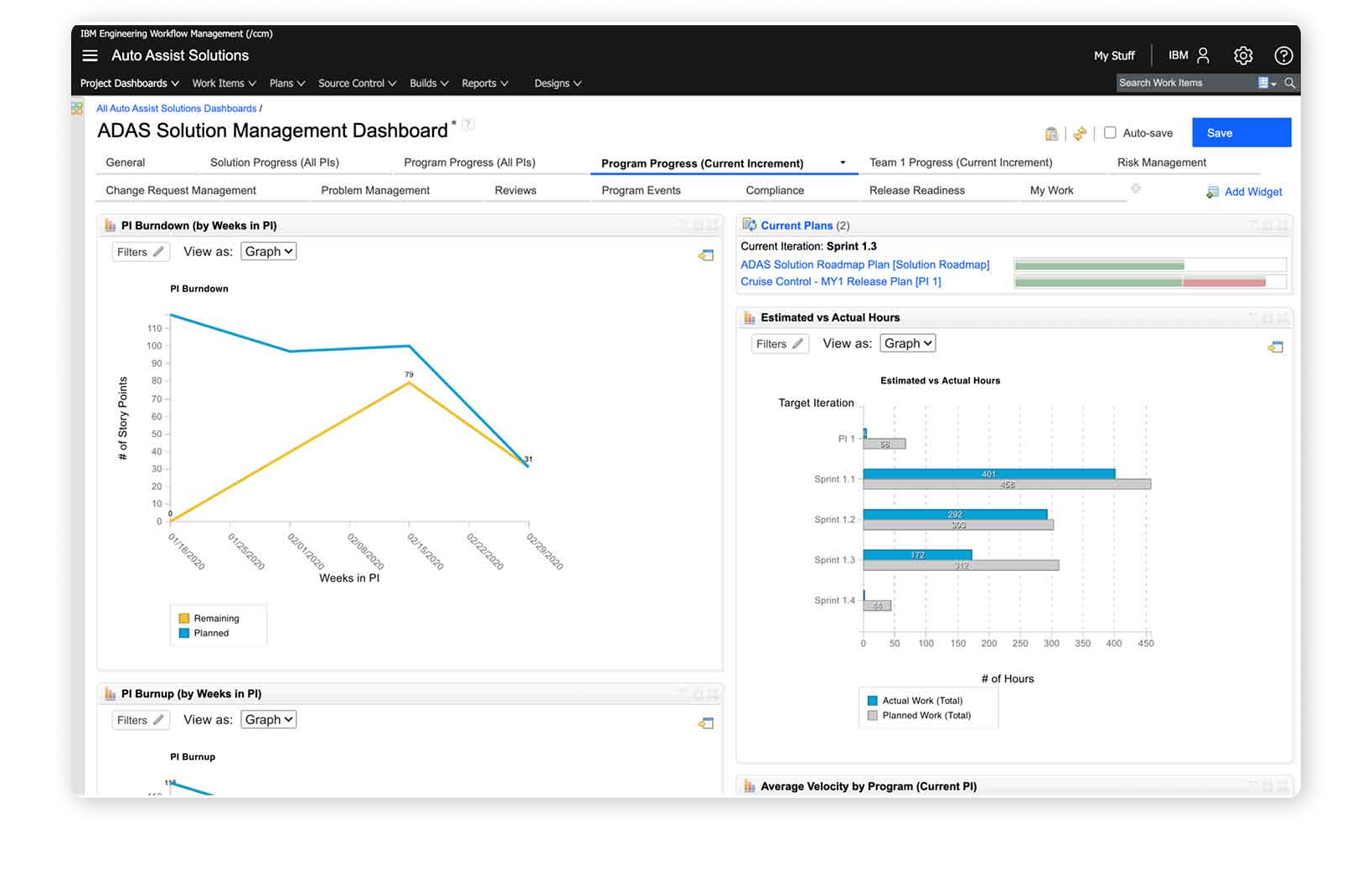
Monitor Progress
The ability to monitor and track progress is crucial for project teams to understand cybersecurity readiness of upcoming milestones and releases, which enables educated decisions for overall release readiness.
- Dashboard with reports to show progress of implementation and test of requirements
- Reports to track problems, risks, change requests and their corrective action
- Widgets to assess release readiness based on quality and competition of iteration objectives.
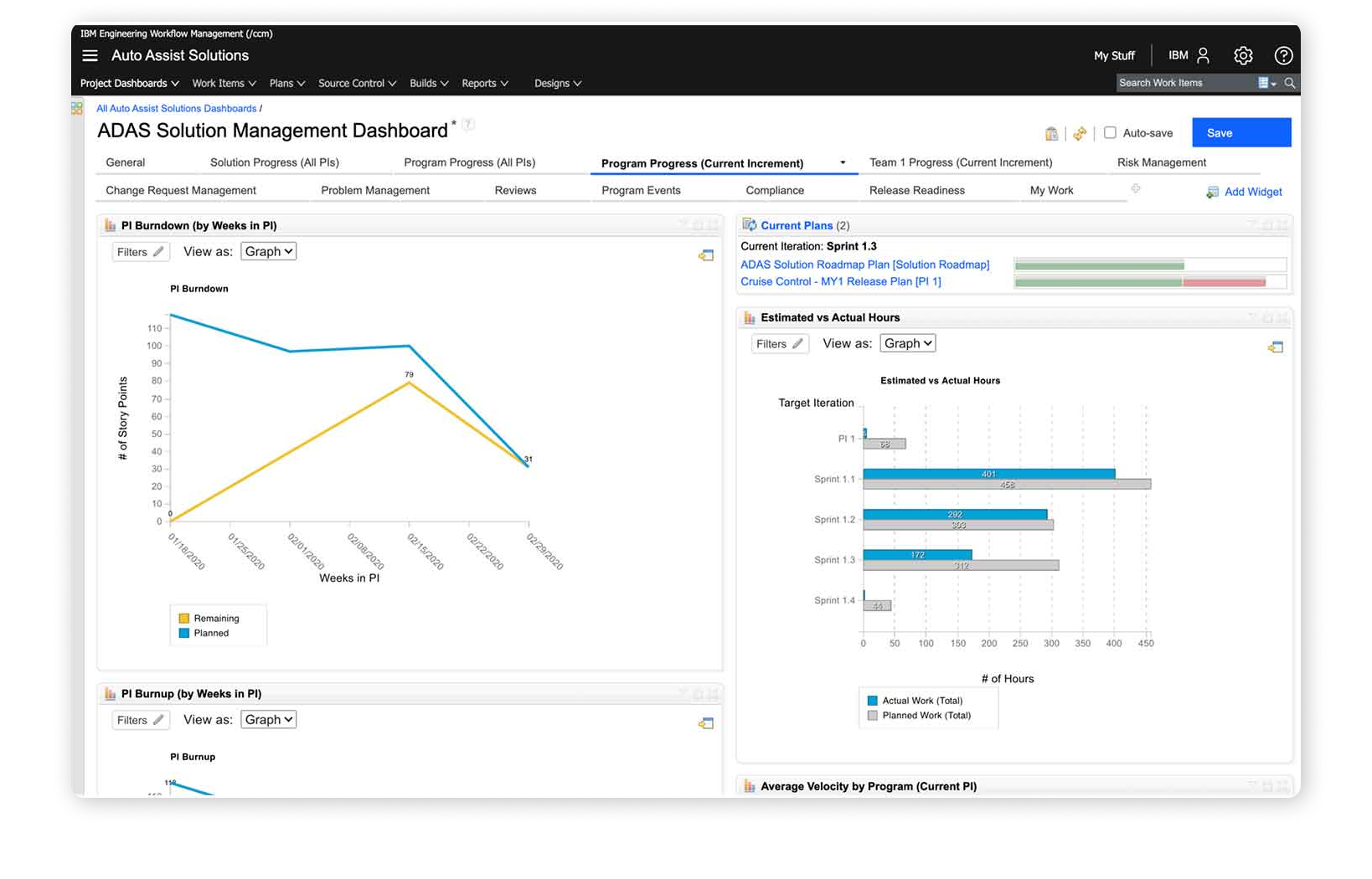
Monitor Progress
The ability to monitor and track progress is crucial for project teams to understand cybersecurity readiness of upcoming milestones and releases, which enables educated decisions for overall release readiness.
- Dashboard with reports to show progress of implementation and test of requirements
- Reports to track problems, risks, change requests and their corrective action
- Widgets to assess release readiness based on quality and competition of iteration objectives.
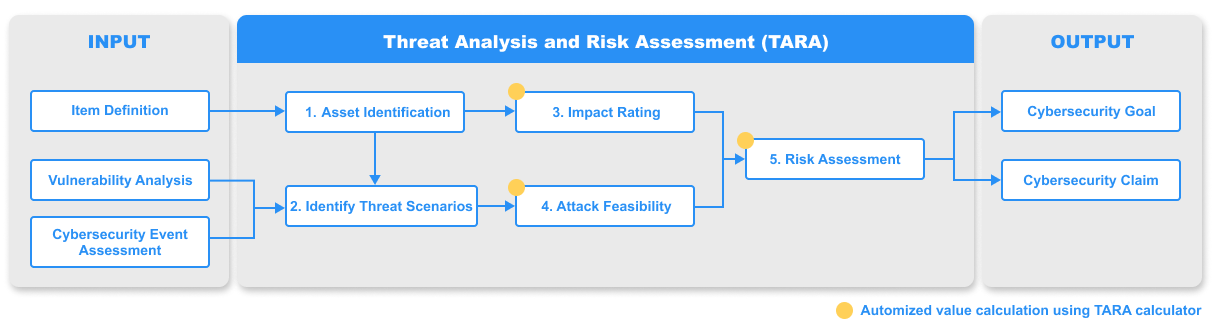
Risk Assessment for Cybersecurity
IBM ELM Cybersecurity Automotive Compliance supports popular Risk Assessment method Threat Analysis and Risk Assessment (TARA) by supporting the features described below:
- Capturing Cybersecurity elements required by ISO 21434 (Assets, Cybersecurity Requirements, Threat Scenario, Attack Paths…).
- Provide inputs for TARA from Cybersecurity Event Assessment and Vulnerability Analysis.
- Automate the calculation of Risk Values by using elements such as possible attack paths and impact of damage scenario.